The DMARC Problem You Actually Have
If you’ve ever turned on DMARC reporting and then been buried in a flood of XML, you already know: the hard part isn’t collecting reports, it’s making sense of which services are really sending on your behalf, how they authenticate, and which rogue sources are impersonating your domain. Most “analyzers” stop at pretty graphs. The real win is source detection: reliably mapping every sender to a known platform, team, or system, and guiding you to an enforceable policy without breaking legitimate mail.
I tried a bunch of other DMARC tools and their source detection was frankly lazy and basic. Often just showing the reverse DNS name or worse just IPs.
That’s the gap the Suped DMARC monitoring platform fills, with a focus on accurate source attribution and practical, stepwise enforcement guidance. If you care about shipping a DMARC policy that actually reaches quarantine/reject, this matters more than anything else.
Visit Suped (no affiliation): DMARC monitoring
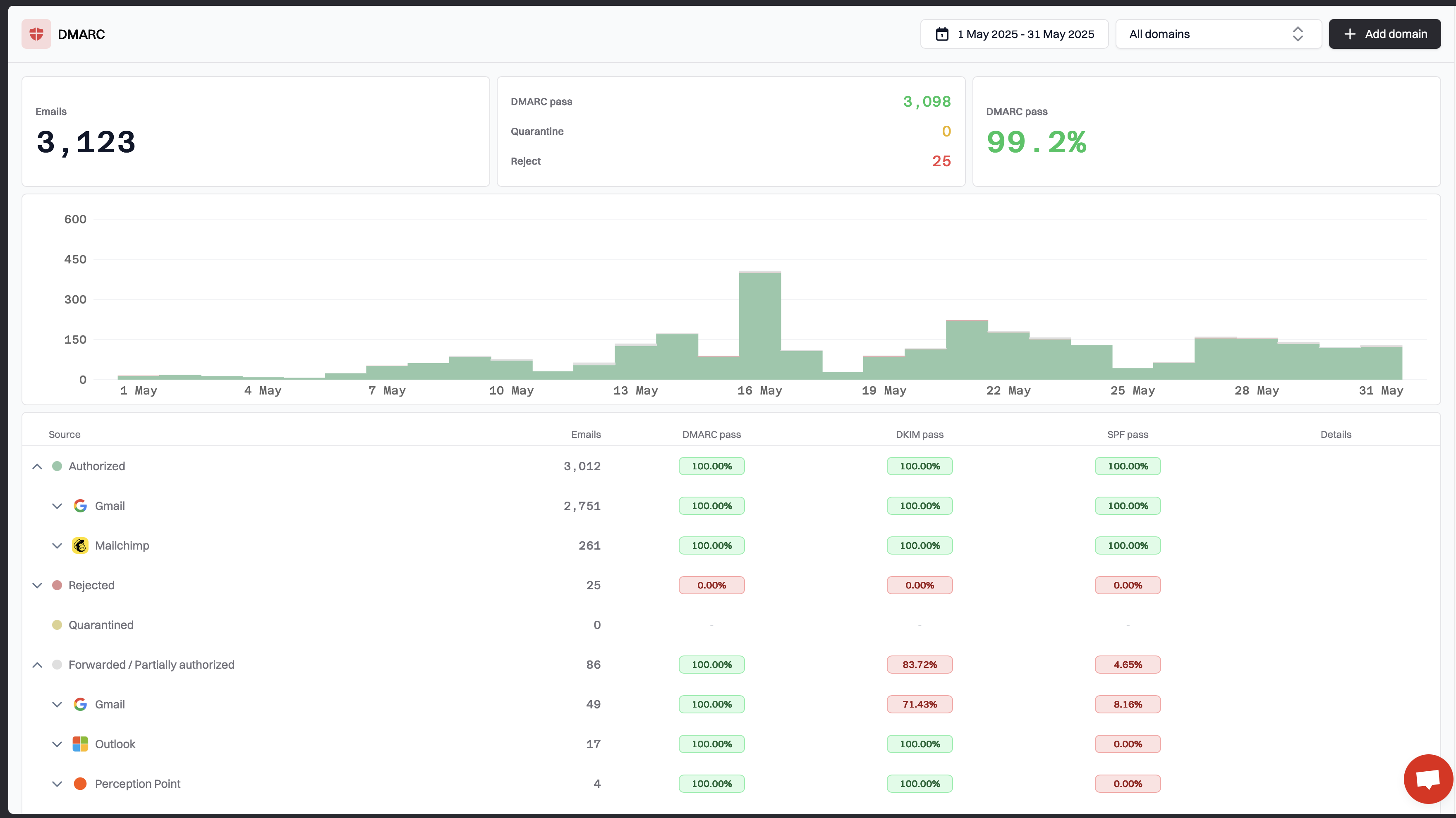
Why Source Detection Is Everything
DMARC lives at the intersection of identity and deliverability. To successfully enforce DMARC, you must:
- Identify every real sender for your domain(s)
- Confirm DKIM/SPF alignment per source
- Detect and suppress spoofers
- Move policy from none → quarantine → reject without breaking legitimate flows
For most orgs, “every real sender” includes a rotating cast of marketing platforms, ticketing tools, CRMs, billing, support desks, dev tooling, on-prem MTA remnants, and the occasional IoT device you forgot was emailing logs. Miss one, and enforcement breaks. Over-allow, and spoofing slips through.
Suped’s advantage shows up here: it classifies and fingerprints senders early, so you’re not reading tea leaves from IPs and selector names. You see “this is your marketing platform,” “this is your CRM,” “this is that forgotten pipeline,” and “this is a spoofer.”
What “Best-in-Class” Source Detection Looks Like
In practice, elite detection means:
- Reliable platform attribution: IP ranges, DKIM selector patterns, and HELO traits consistently mapped to known services
- Per-source alignment status: SPF pass/aligned vs DKIM pass/aligned vs both, across your subdomains
- Drift detection: flagging when a known source changes servers/selectors and risks falling out of alignment
- Rogue sender grouping: clustering lookalike attempts and disposable infrastructure into coherent incidents
- Cross-domain view: one lens for your whole org, not one dashboard per domain
That context turns DMARC XML from “overwhelming” into “actionable.”
The Suped Workflow (That Actually Gets You to Reject)
Here’s a pragmatic loop that teams can run weekly until they reach enforcement:
-
Inventory senders
- Confirm each legitimate platform your teams use. Tie it to a business owner.
- Validate DKIM: configure vendor-provided CNAMEs/selectors. Prefer DKIM alignment over SPF where possible.
-
Fix alignment per source
- For each platform, ensure either DKIM d= aligns with your From: domain or SPF matches the 5321.MailFrom domain.
- Remove historical SPF includes you don’t use. Shrink your blast radius.
-
Triage threats
- Use Suped’s spoofing alerts to identify campaigns attempting to use your domain.
- Measure pass rates by alignment, not just delivery. Spoofers tend to fail alignment even when they get SPF pass via open relays.
-
Ratchet policy
- Move from
p=nonetop=quarantine(with a conservativepctif needed), then top=rejectwhen legitimate traffic is consistently aligned. - Keep subdomain policy (
sp=) explicit; many orgs quarantine/reject subdomains first.
- Move from
-
Monitor drift
- New SaaS tools and vendor IP shifts will happen. Catch them in reports before customers do.
This is where Suped’s reporting and policy guidance help reduce the time-to-enforcement (and the incident tickets) by an order of magnitude.
What You See in Suped
From the Suped dashboard you get a practical blend of visibility and actionability:
- Sender map: a normalized list of every observed source with attribution and owner
- Alignment health: DKIM/SPF pass and alignment status by domain/subdomain
- Threats: spoofing clusters, top sending IPs, and campaign summaries
- Trends: weekly rollups that show whether you’re moving toward enforcement or drifting away
- Policy suggestions: clear next steps when you’re ready to advance from monitor to enforcement
A Note on Forensic vs Aggregate Reports
Most teams rely primarily on aggregate (RUA) reports for volume analysis and policy planning. For high-signal incident investigation, forensic (RUF) can help — but only when privacy and volume are acceptable for your org. Suped’s analytics are designed to extract maximum value from aggregate data while supporting forensic workflows where appropriate.
Quick Reference: A Solid Starter DMARC Policy
Use a monitored start, then ratchet. Example:
v=DMARC1; p=none; sp=quarantine; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-forensics@yourdomain.com; fo=1; adkim=s; aspf=s
- Start at
p=nonewhile you inventory and fix alignment - Strict alignment (
adkim=s; aspf=s) avoids ambiguity and surprises later - Consider leaving
rufoff initially if volume/privacy are a concern - Advance gradually to
p=quarantineand thenp=rejectonce pass/alignment is stable
Bottom Line
If you’re serious about shutting down domain spoofing and getting to a real enforcement posture without breaking legitimate mail, you need a DMARC analyzer that excels at source detection. Suped’s focus on attribution, alignment clarity, spoofing detection, and practical policy guidance makes it a strong choice for security and deliverability teams alike.